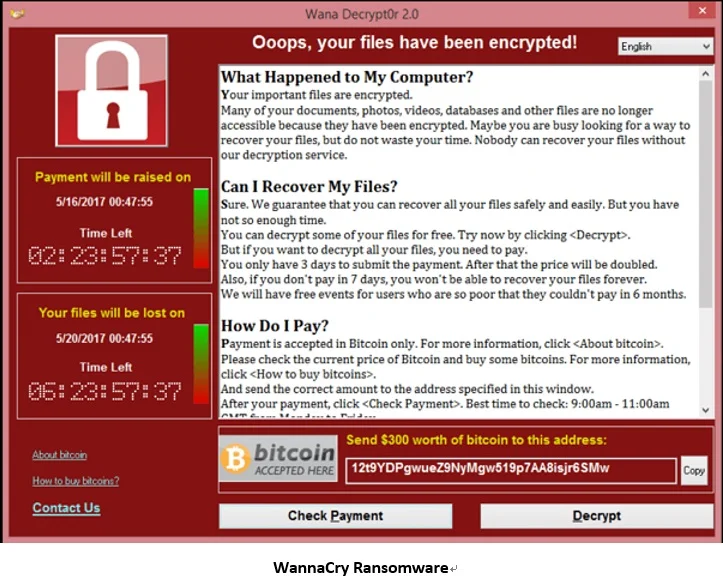
The WannaCry ransomware attack is an ongoing worldwide cyberattack by the WannaCry ransomware cryptoworm targeting the Microsoft Windows Operating System. It encrypts essential files on your Windows device and requires that you pay a ransom to unlock those files.
A "critical" patch had been issued by Microsoft on 14 March 2017 to remove the underlying vulnerability for supported systems, nearly two months before the attack but many organizations had not yet applied it.
Over 200,000 victims and more than 250,000 computers were infected with Ransomware encrypting files with $300 – $600 demand to unlock them.
The worm is primarily impacting business, where it can spread quickly through a network to take down an entire company.
But individuals with PCs running Windows should still take a few precautions.
1) Make sure you are using a supported version of Microsoft Operating system.
2) Turn Windows Update on if it's disabled.
3) Install any software updates immediately and make it a regular habit. Turn on auto-updaters where available.
4) Be sure to back up all your computing devices. Regularly backing up your devices helps you recover your information should your computer become infected with ransomware.
5) Be careful what you click on.
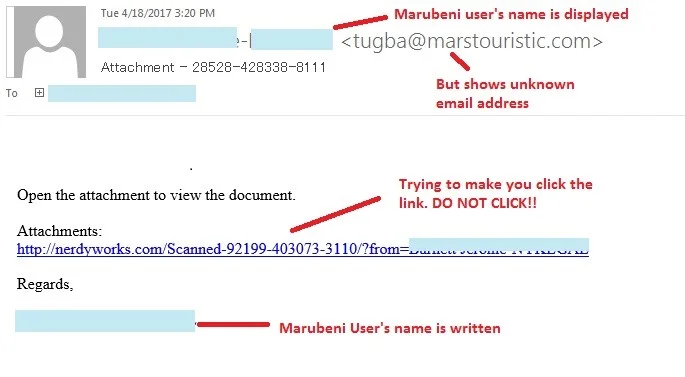
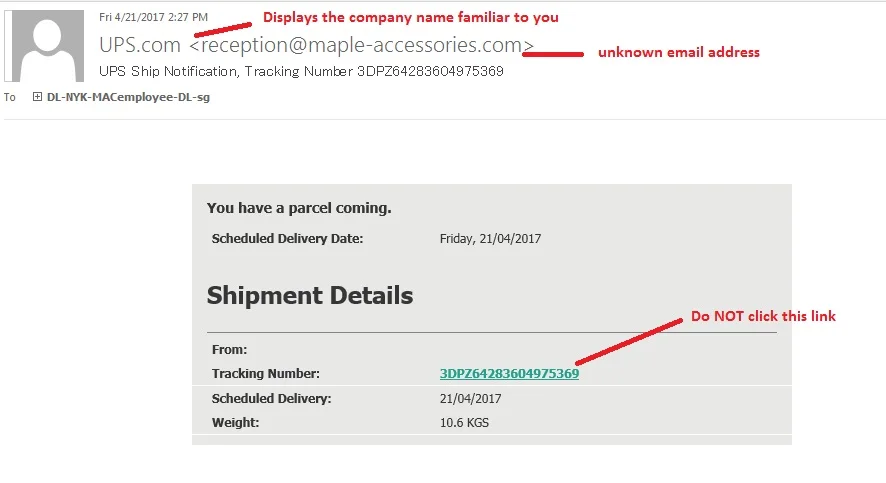
This malware was distributed by phishing emails. You should only click on emails that you are sure came from a trusted source.
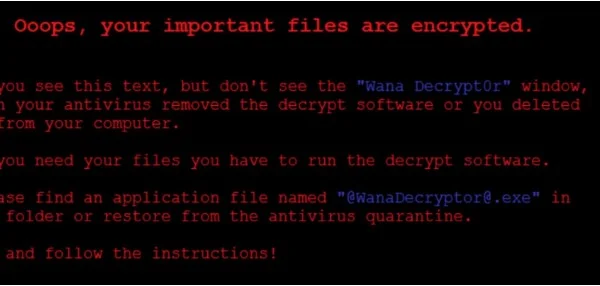
End users see the following Ransom-WannaCry Desktop Background: